Antikeymagic V.14.01 Tab: Specials – Picture Demo – Liste Laufwerke von A bis Z.
//
Antikeymagic V.14.01 Tab: Specials – Picture Demo – List drives from A to Z.
The Hook on WSCSVC and ChatGPT, Admin needs full authority, not the Operating System. Anti-Fascism/Anti-Totalitarism starts in your O.S.
//
Der Haken auf WSCSVC und ChatGPT, der Administrator benötigt die volle Autorität, nicht das Betriebssystem. Anti-Faschismus/Anti-Totalitarismus beginnt in deinem Betriebssystem.
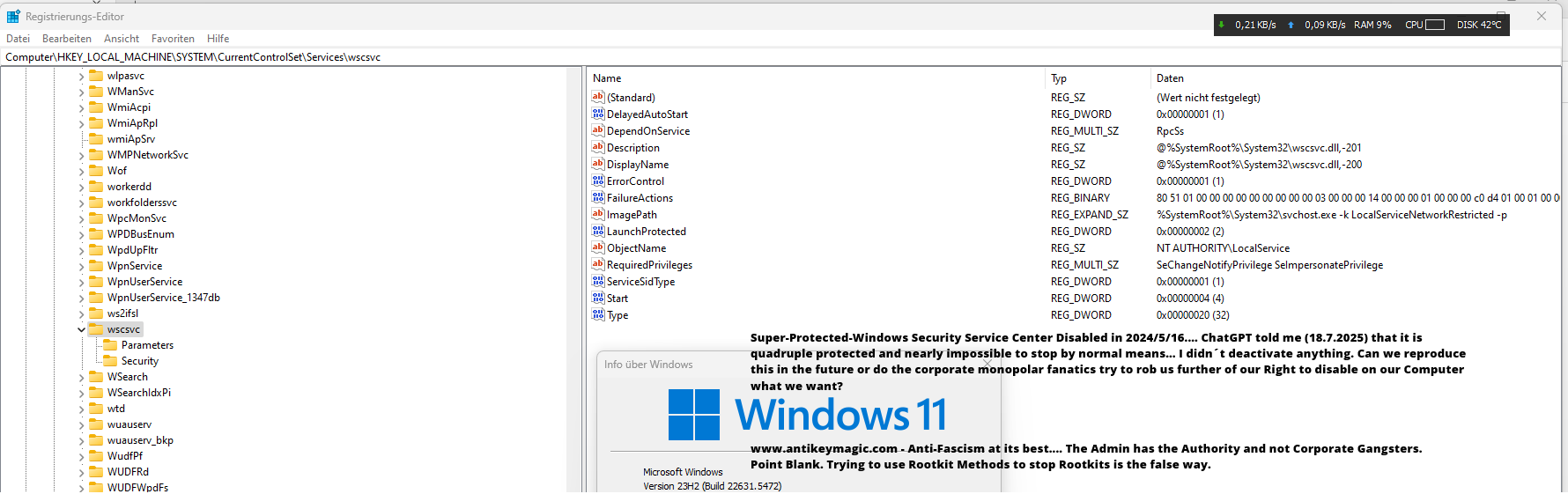 You also could rename the dll by external means (via another os) but this will destroy the ability to start Windows 11…They use aggressive hooking techniques to prevent the average Joe Doe from doing anything against their Digital Dictation that blocks intuitive workflow.
You also could rename the dll by external means (via another os) but this will destroy the ability to start Windows 11…They use aggressive hooking techniques to prevent the average Joe Doe from doing anything against their Digital Dictation that blocks intuitive workflow.
//
Du könntest die dll auch extern umbenennen (über ein anderes Betriebssystem), aber dadurch wird die Möglichkeit zerstört, Windows 11 zu starten… Sie verwenden aggressive Hooking-Techniken, um den Durchschnittsbürger daran zu hindern, etwas gegen ihre digitale Bevormundung zu tun, die den intuitiven Arbeitsablauf blockiert.
Ja, Antikeymagic existiert noch, 20-jähriges Jubiläum.
//
20-Jahres-Jubiläum von Antikeymagic, wenige kamen in den Genuss der vollen Genialität dieses Multifunktionstools.
Viele böse Sabotagegruppen/Geheimdienste und Gang Stalker Schattenregierungen versuchten über Jahrzehnte hinweg das Unaufhaltsame mit ihren Angriffen zu stoppen.
//
20-Years-Jubilee of Antikeymagic, few were able to enjoy the full genius of this multifunctional tool.
Many evil saboteur groups/secret services and gang stalking shadow govs tried over decades to stop the unstoppable with their assaults.
A New Function to keep System Performance clean for CPU-Z Bench freaks… It gives the ultra-high-speed Guard just 1 round and does not stress the CPU nonstop. Functional from V.13.17 on upwards.
//
Eine neue Funktion, um die Systemleistung für CPU-Z-Bench-Freaks sauber zu halten … Sie gewährt dem Ultra-High-Speed Wächter nur eine Runde und belastet die CPU nicht ununterbrochen. Funktioniert ab V.13.17 aufwärts.
24.5.2024: Security Check 3.01 Updated. A Part of Antikeymagic V.13.17 – unlocked starting up from Bronze Private Editions upwards.
/
Sicherheitscheck 3.01 aktualisiert. Ein Teil von Antikeymagic V.13.17 – freigeschaltet ab Bronze Privat Editionen aufwärts.
Windows Defender in Windows 11 behaves Malware-Like…
It forces itself automatically over the free will of the user which is Malware-Like, it bypasses your decision to shut it down, which is Malware-Identical. It uses Shadow Table Hooks to prevent the Administrator from stopping it, which is Malware-Identical. It attacks 3rd Party Security Tools to stop them from finding their Malware-Tactics which is Malware-Like. It automatically reactivates itself against the Will of the Administrator which is Malware-Identical and Totalitarian. The Admin ought to have full decision control over his Operation System, we are experienced enough to take full control over our systems.
//
Der Windows Defender in Windows 11 verhält sich Malware-ähnlich…
Er drängt sich automatisch über den freien Willen des Benutzers, was Malware-ähnlich ist, er umgeht deine Entscheidung, ihn abzuschalten, was Malware-identisch ist. Er verwendet Schattentabellenhaken, um zu verhindern, dass der Administrator ihn stoppen kann, was Malware-identisch ist. Er greift Sicherheitstools von Drittanbietern an, um sie daran zu hindern, seine Malware-Taktiken zu finden, was Malware-ähnlich ist. Er reaktiviert sich automatisch gegen den Willen des Administrators, was mit Malware identisch und totalitär ist. Der Administrator sollte die volle Entscheidungskontrolle über sein Betriebssystem haben. Wir sind erfahren genug, um die volle Kontrolle über unsere Systeme zu übernehmen.


AVZ 4.46 Proves the Hooks:
Scanning started at 16.05.2024
Heuristic microprograms loaded: 412
AVZ is run with administrator rights (+)
1. Searching for Rootkits and other software intercepting API functions
1.1 Searching for user-mode API hooks
Analysis: kernel32.dll, export table found in section .rdata
Function kernel32.dll:ReadConsoleInputExA (1163) intercepted, method – ProcAddressHijack.GetProcAddress ->76C1F421->75E38A50
Function kernel32.dll:ReadConsoleInputExW (1164) intercepted, method – ProcAddressHijack.GetProcAddress ->76C1F454->75E38A80
Analysis: ntdll.dll, export table found in section .text
Function ntdll.dll:NtCreateFile (301) intercepted, method – ProcAddressHijack.GetProcAddress ->77A66D60->70065210
Function ntdll.dll:NtSetInformationFile (613) intercepted, method – ProcAddressHijack.GetProcAddress ->77A66A80->70065380
Function ntdll.dll:NtSetValueKey (646) intercepted, method – ProcAddressHijack.GetProcAddress ->77A66E10->700653F0
Function ntdll.dll:ZwCreateFile (1879) intercepted, method – ProcAddressHijack.GetProcAddress ->77A66D60->70065210
Function ntdll.dll:ZwSetInformationFile (2189) intercepted, method – ProcAddressHijack.GetProcAddress ->77A66A80->70065380
Function ntdll.dll:ZwSetValueKey (2222) intercepted, method – ProcAddressHijack.GetProcAddress ->77A66E10->700653F0
Analysis: user32.dll, export table found in section .text
Function user32.dll:CallNextHookEx (1536) intercepted, method – ProcAddressHijack.GetProcAddress ->7785E5D0->700650F0
Function user32.dll:EnumWindows (1774) intercepted, method – ProcAddressHijack.GetProcAddress ->7787D090->70065E30
Function user32.dll:GetWindowThreadProcessId (2011) intercepted, method – ProcAddressHijack.GetProcAddress ->7785E7A0->70065E60
Function user32.dll:IsWindowVisible (2094) intercepted, method – ProcAddressHijack.GetProcAddress ->77854CC0->70065E90
Function user32.dll:MessageBoxA (2148) intercepted, method – ProcAddressHijack.GetProcAddress ->778AB310->70067EC0
Function user32.dll:MessageBoxExA (2149) intercepted, method – ProcAddressHijack.GetProcAddress ->778AB360->70067F20
Function user32.dll:MessageBoxExW (2150) intercepted, method – ProcAddressHijack.GetProcAddress ->778AB390->70067F80
Function user32.dll:MessageBoxIndirectA (2151) intercepted, method – ProcAddressHijack.GetProcAddress ->778AB3C0->70067FE0
Function user32.dll:MessageBoxIndirectW (2152) intercepted, method – ProcAddressHijack.GetProcAddress ->778AB500->70068030
Function user32.dll:MessageBoxW (2155) intercepted, method – ProcAddressHijack.GetProcAddress ->778AB830->70068090
Function user32.dll:SetWindowsHookExW (2400) intercepted, method – ProcAddressHijack.GetProcAddress ->77862C50->70065460
Function user32.dll:ShowWindow (2409) intercepted, method – ProcAddressHijack.GetProcAddress ->77864E80->700680F0
Function user32.dll:Wow64Transition (1504) intercepted, method – CodeHijack (not defined)
Analysis: advapi32.dll, export table found in section .text
Function advapi32.dll:CveEventWrite (1234) intercepted, method – ProcAddressHijack.GetProcAddress ->75889300->75E3C940
Function advapi32.dll:I_ScRegisterPreshutdownRestart (1366) intercepted, method – ProcAddressHijack.GetProcAddress ->7588A084->75AEAE50